Building my own Agentic SOC Analyst
I taught GPT-5 to hunt threats. It's better than me.
The Breaking Point
I used to joke that I wasn’t a SOC analyst—I was a professional false-positive investigator. Three hours into a Sentinel alert, only to find out it was nothing. Then do it all over again tomorrow. And the next day.
One night, around 2 AM, I caught myself staring at the same Entra ID sign-in log for the third time, wondering if my eyes were inventing anomalies. That’s when it hit me: the logs weren’t breaking me. The process was.
So I decided to automate myself out of the pain.
What I Built
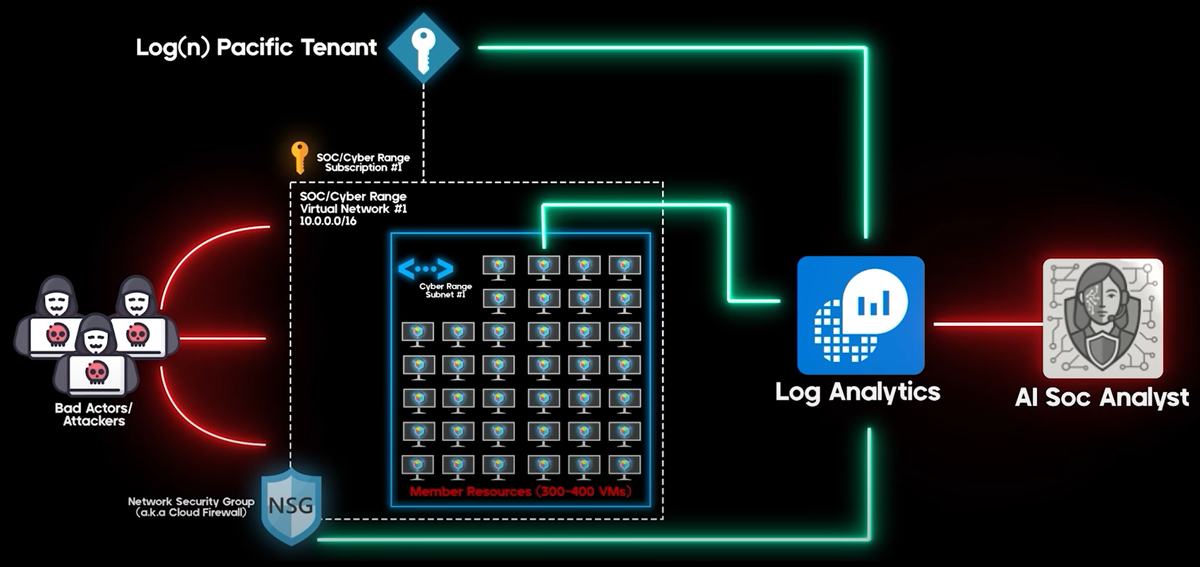
I created an AI agent that thinks like a senior threat hunter and plugs directly into Log Analytics.
- Ingests: MDE & MDO logs, Entra ID events, Azure Activity
- Analyzes: Maps findings to MITRE ATT&CK, scores confidence
- Enriches: Auto-scans IOCs via VirusTotal
The Numbers
- Before: 2–3 hours per incident
- After: 15 minutes
- False positives: Down 40%
- My sanity: Restored
Now, instead of burning an evening on a dead-end alert, I can actually log off, cook dinner, and still trust that nothing slipped by.
How It Works
The agent doesn't just search logs—it understands them. It spots process injection, catches beaconing patterns, identifies privilege escalation chains.
Things I'd miss at 2 AM, it catches instantly.
Get It
Stop being a human log parser.
Start being the analyst who actually gets to sleep.
👉 GitHub: agentic-soc-analyst
Your future self will thank you.